5 Minute Read
Security in Web Development
What You Need To know
Security is an extremely crucial and pivotal aspect of web development, and it is of utmost importance to guarantee the safeguarding of web applications against a multitude of potential threats.
This guide delves into the generalities of security, elaborates on the wide array of common threats that exist, provides insight into the best practices that should be followed, and sheds light on the emerging trends in the ever-evolving field of web development security.
By thoroughly understanding the measures discussed in this comprehensive guide and doing your own research, you can help to ensure the fortification of your web applications and mitigate the risks associated with cyber attacks, data breaches, and other malicious activities that can wreak havoc on the digital landscape.
In an age where cybercrime is increasingly prevalent, it is imperative for web developers to stay well-informed and proactive in order to stay one step ahead of potential threats and protect the sensitive information of users.
With the guidance and knowledge provided within this guide, you'll gain a deeper general understanding of security in website development and it's significance.
Let's get right down to it, shall we!

Table of Contents
- Importance of Security in Web Development
- Common Web Security Threats
- Web Security Best Practices
- Authentication and Authorization
- Web Application Firewalls (WAF)
- Security Testing
- Keeping Dependencies Secure
- Incident Response and Handling
- Privacy Concerns and Data Protection
- Compliance with Regulations
- Emerging Trends in Web Security
- Conclusion
Importance of Security in Web Development
Security is of utmost importance when it comes to ensuring the integrity, availability, and confidentiality of web applications. Without a doubt, a breach in security can have dire consequences that extend far beyond just compromising user data.
In fact, it can inflict serious damage on the reputation and credibility of the organization responsible. As the digital landscape becomes increasingly complex and cyber threats grow more sophisticated, it is imperative for businesses to prioritize incorporating robust security measures into their web development processes.
When we talk about security in the context of web applications, we are referring to the implementation of various strategies and protocols that aim to safeguard sensitive information, prevent unauthorized access, and mitigate the risks posed by cybercriminals. By taking proactive measures to ensure the security of web applications, organizations can protect their users' data from falling into the wrong hands and maintain the trust of their clientele.
One of the primary reasons why security is so crucial in web development is because web applications often deal with sensitive information such as personal details, financial data, and confidential records. Any compromise in security can lead to devastating consequences, including identity theft, financial loss, and even legal repercussions.
Moreover, users are becoming increasingly aware of the importance of their online privacy and are more likely to choose web applications that prioritize security.
In addition to the potential harm caused to users, a security breach can have severe ramifications for the organization itself. The negative impact on the company's reputation can be significant, resulting in a loss of trust, credibility, and ultimately, customers. It takes a considerable amount of time and effort to rebuild a tarnished reputation, and in some cases, the damage can be irreparable.
As the field of cybersecurity continues to evolve, so do the tactics employed by cybercriminals. They are constantly finding new ways to exploit vulnerabilities in web applications, making it crucial for businesses to stay one step ahead by incorporating robust security measures.
This can involve implementing secure coding practices, regularly updating and patching software, conducting thorough security audits, and employing advanced encryption techniques.
Moreover, organizations must not view security as a one-time effort but rather as an ongoing process. With the rapid advancements in technologies, new threats are constantly emerging, and staying up to date with the latest security measures is essential.
This requires businesses to invest in regular security training for their development teams and to stay informed about current threats and vulnerabilities.

Common Web Security Threats
Cross-Site Scripting (XSS)
Definition: XSS occurs when an attacker injects malicious scripts into web pages, which are then executed by the user's browser.
Prevention:
- Input validation and sanitization.
- Content Security Policy (CSP) implementation.
Cross-Site Request Forgery (CSRF)
Definition: CSRF involves tricking the victim into submitting a malicious request. Attackers forge requests from the victim's browser, causing actions on the victim's behalf.
Prevention:
- Anti-CSRF tokens.
- SameSite cookie attribute.
SQL Injection
Definition: SQL injection occurs when an attacker injects malicious SQL queries into input fields, potentially gaining unauthorized access to the database.
Prevention:
- Parameterized queries.
- Input validation and sanitization.
Security Misconfigurations
Definition: Security misconfigurations arise when developers leave unintentional vulnerabilities due to misconfigured settings, permissions, or default configurations.
Prevention:
- Regular security audits.
- Follow secure coding guidelines.
Insecure Direct Object References (IDOR)
Definition: IDOR occurs when an attacker can access or modify objects, such as files or database entries, without proper authorization.
Prevention:
- Implement proper access controls.
- Use indirect references instead of direct object references.
Web Security Best Practices
Input Validation and Sanitization
- Validate and sanitize user input to prevent malicious data entry.
- Use input validation frameworks and libraries.
Session Management
- Use secure and random session identifiers.
- Implement session timeout mechanisms.
- Store session data securely.
HTTPS Implementation
- Encrypt data in transit using HTTPS.
- Obtain and install SSL/TLS certificates.
- Ensure secure communication between clients and servers.
Content Security Policy (CSP)
- Define and implement a Content Security Policy.
- Restrict the sources from which content can be loaded.
- Mitigate the risks of XSS attacks.
Cross-Origin Resource Sharing (CORS)
- Implement CORS headers to control which domains can access resources.
- Use appropriate CORS settings based on the application's requirements.
Authentication and Authorization
Password Security
- Enforce strong password policies.
- Store passwords securely using hashing algorithms.
- Encourage password management best practices.
Multi-Factor Authentication (MFA)
- Implement MFA to add an extra layer of security.
- Use methods like SMS, email, or authenticator apps for multi-factor verification.
Role-Based Access Control (RBAC)
- Assign roles and permissions based on the principle of least privilege.
- Regularly review and update access controls.
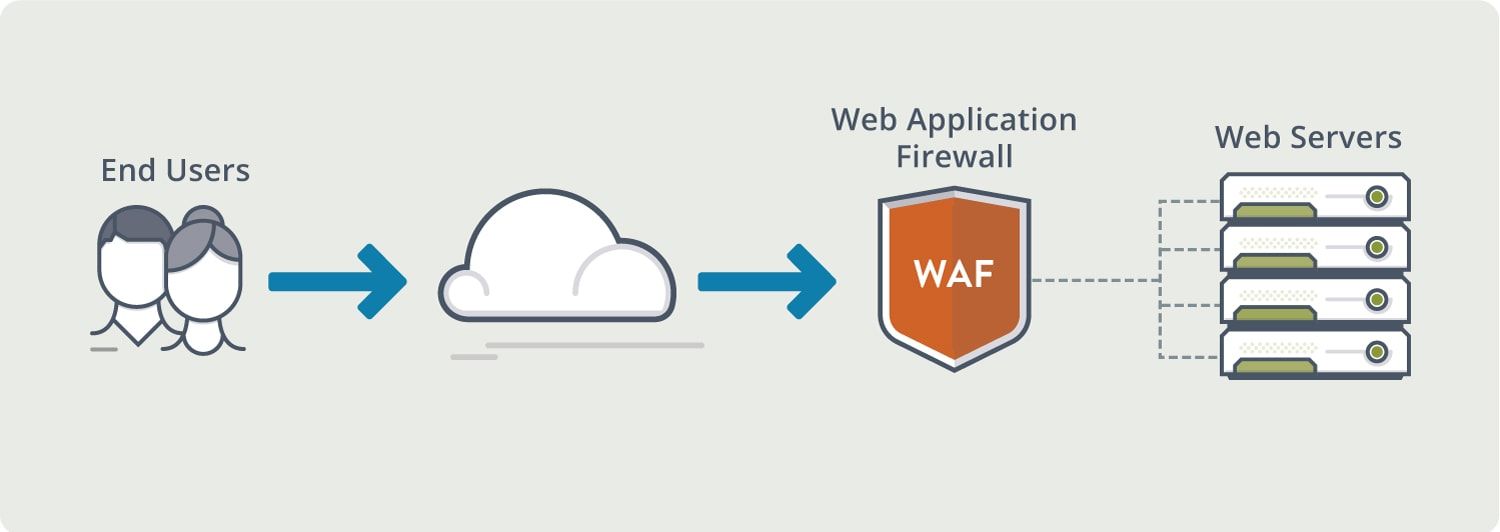
Web Application Firewalls (WAF)
Definition:
A Web Application Firewall (WAF) is a security solution that monitors, filters, and blocks HTTP traffic between a web application and the Internet.
Benefits
- Protects against common web application attacks.
- Filters malicious traffic and prevents unauthorized access.
Implementation
- Deploy a WAF as part of the network infrastructure.
- Regularly update and configure the WAF to adapt to evolving threats.
Security Testing
Types of Security Testing
- Vulnerability Scanning: Automated tools scan for known vulnerabilities.
- Penetration Testing: Simulates real-world attacks to identify vulnerabilities.
- Code Review and Static Analysis: Manual or automated analysis of code for security issues.
Penetration Testing
- Conduct regular penetration testing to identify and address vulnerabilities.
- Engage third-party security experts for comprehensive assessments.
Keeping Dependencies Secure
Dependency Scanning
- Regularly scan and update third-party dependencies.
- Monitor for security advisories related to dependencies.
Regular Updates
- Stay informed about security updates for all components.
- Establish a process for promptly applying updates.
Incident Response and Handling
Incident Response Plan
- Develop and document an incident response plan.
- Define roles and responsibilities for incident response team members.
Communication Protocols
- Establish clear communication channels during security incidents.
- Notify relevant stakeholders promptly and accurately.
Privacy Concerns and Data Protection
Data Encryption
- Encrypt sensitive data at rest and in transit.
- Use strong encryption algorithms and key management practices.
Privacy by Design
- Integrate privacy considerations into the development lifecycle.
- Minimize data collection and only retain necessary information.

Compliance with Regulations
GDPR (General Data Protection Regulation)
- Ensure compliance with GDPR principles, including data protection by design and default.
- Obtain explicit consent for data processing activities.
PCI DSS (Payment Card Industry Data Security Standard)
- Implement PCI DSS requirements for handling payment card information.
- Regularly conduct security assessments to maintain compliance.
Emerging Trends in Web Security
Here are some emerging trends in web security.
Zero Trust Security
- Adopt a Zero Trust model that assumes no implicit trust.
- Verify and authenticate every user and device attempting to connect to the network.
AI and Machine Learning in Security
- Leverage AI and machine learning for threat detection and response.
- Implement anomaly detection to identify unusual patterns.
Conclusion
Web development security is an ongoing and dynamic process that requires a proactive approach. By integrating security best practices, staying informed about emerging threats, and adopting the latest security technologies, developers can build and maintain secure web applications.
Regular testing, incident response planning, and compliance with regulations are crucial components of a robust security strategy.
As the web landscape evolves, it is imperative for developers to adapt and prioritize security to protect both users and the organization's assets.